Getting Started
To configure trulyMEid’s multi-factor authentication (MFA) provider for Active Directory Federation Services (AD FS), you’ll need
- Admin access to the AD FS server
- the trulyMEid AD FS install package (contact support@trulyMEid.com for your download link)
- your specific configuration from your trulyMEid support representative
Install
Once you have all three items, login to the AD FS server and extract the install package zip file to C:\Install. (You can create any temporary directory you want – the example uses C:\Install.)
Right click on the “trulyMEidConfig” executable and select “Run as administrator.”
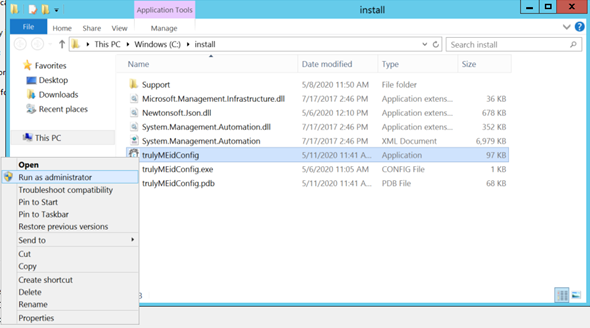
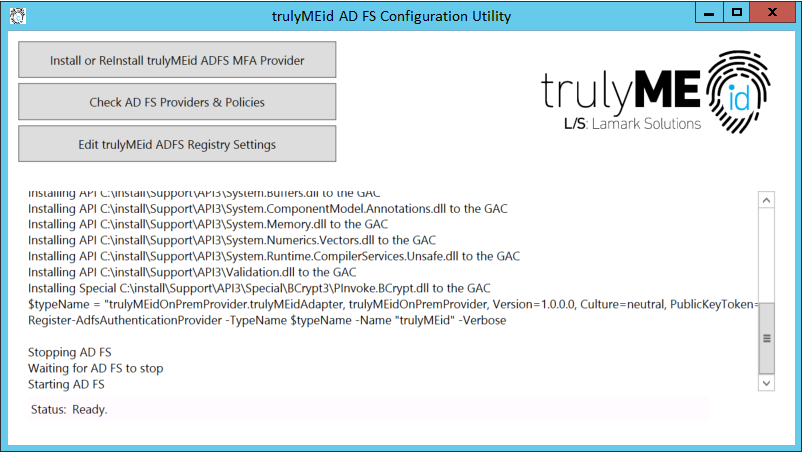
Clicking the “Install or Reinstall trulyMEid ADFS MFA Provider” will install the trulyMEid and requisite support dlls into the GAC on the local machine. It will also register trulyMEid as a MFA provider in AD FS.
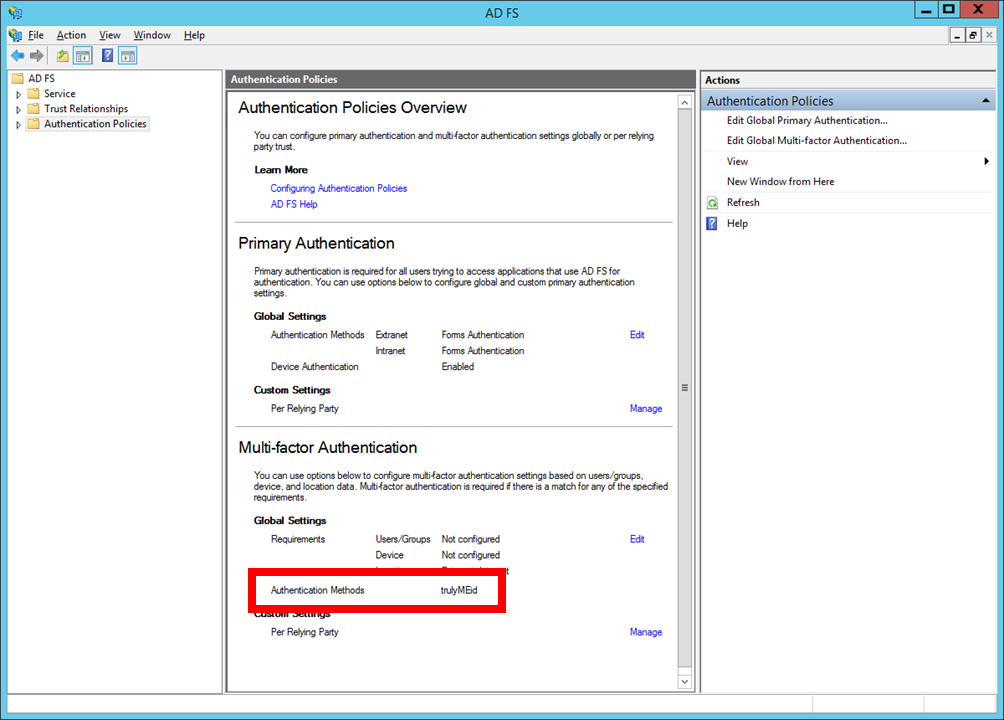
At this point, you can verify that trulyMEid is available to AD FS by opening the AD FS admin console and looking at the Authentication Policies page.
Configure trulyMEid
Clicking the “Edit trulyMEid ADFS Registry Settings” button sets up default registry entries and provides a view into the trulyMEid registry settings.
Relying Party Configuration
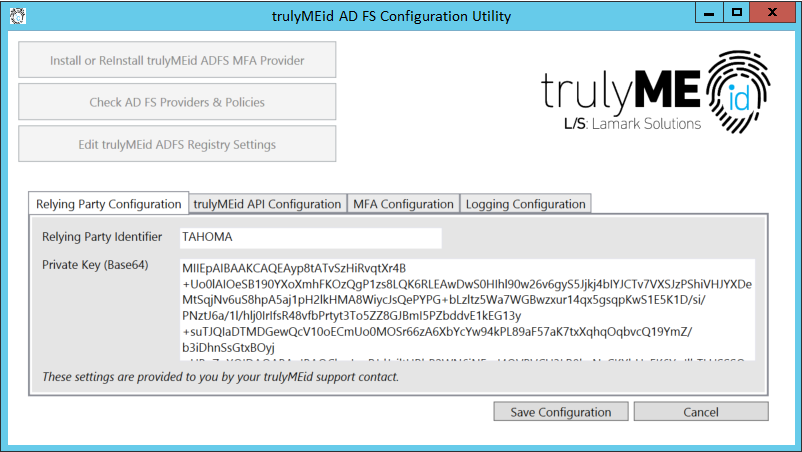
Relying Party Identifier is what identifies your organization to trulyMEid. This value will be given to you by your trulyMEid support representative. (HKLM\SOFTWARE\trulyMEid\RelyingPartyIdentifier)
Private Key (Base 64) is a unique private key for your organization. This value will be given to you by your trulyMEid support representative. (HKLM\SOFTWARE\trulyMEid\RelyingPartyPrivateKeyBase64)
trulyMEid API Configuration
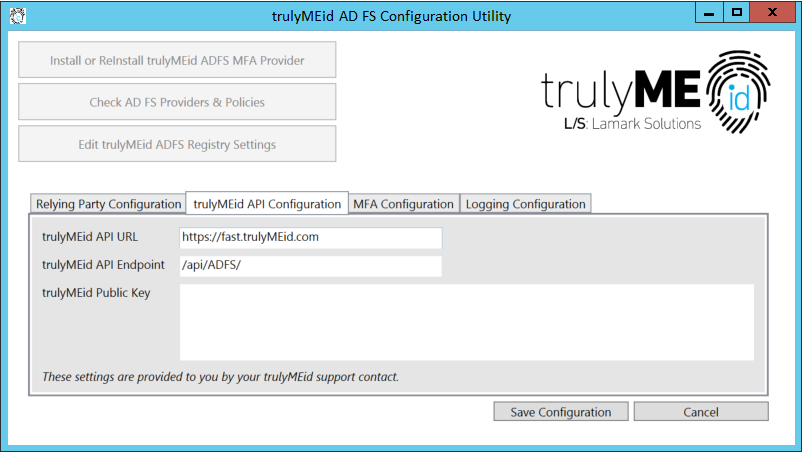
trulyMEid API URL is the base URL for the trulyMEid AD FS API. Unless otherwise specified by your trulyMEid support representative, this value should be “https://fast.trulyMEid.com” (without a trailing “/”).(HKLM\SOFTWARE\trulyMEid\trulyMEidBaseUrl)
trulyMEid API Endpoint is the API endpoint for the trulyMEid AD FS API. Unless otherwise specified by your trulyMEid support representative, this value should be “/api/ADFS/” (with a trailing “/”).(HKLM\SOFTWARE\trulyMEid\trulyMEidEndpoint)
trulyMEid Public Key is a unique public key for interactions between trulyMEid and your organization. This value will be given to you by your trulyMEid support representative. (HKLM\SOFTWARE\trulyMEid\trulyMEidPublicKeyBase64)
MFA Configuration
These configuration items are included in MFA requests to the trulyMEid cloud and are included in trulyMEid’s audit logs. They do not affect performance or user interface. They may be useful in parsing trulyMEid’s cloud audit logs for your organization.
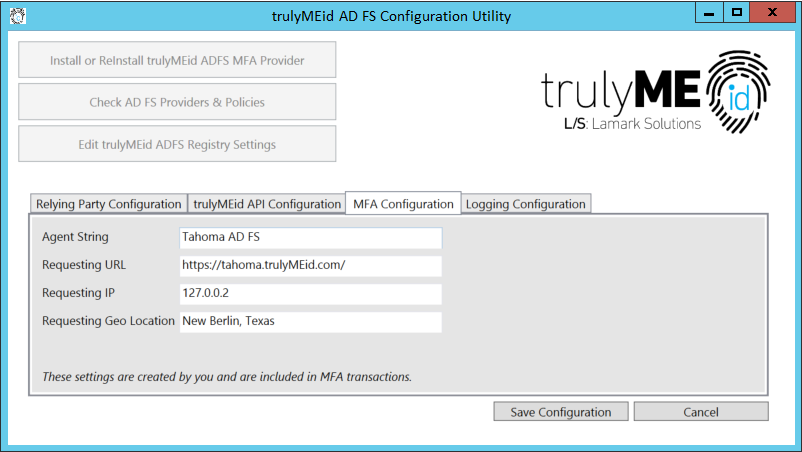
Agent String typically refers to a browser and in other audit events it will contain the browser information. Use this field to identify transactions originating from AD FS. (HKLM\SOFTWARE\trulyMEid\MfaAgent)
Requesting URL typically identifies a web-based application. Use this field to identify transactions originating from AD FS.(HKLM\SOFTWARE\trulyMEid\MfaUrl)
Requesting IP typically identifies the IP address of a transaction. Use this field to identify transactions originating from AD FS.(HKLM\SOFTWARE\trulyMEid\MfaIP)
Requesting Geo Location is typically obtained through a reverse IP lookup to identify a geographic location. Use this field to identify transactions originating from AD FS. (HKLM\SOFTWARE\trulyMEid\MfaGeo)
Logging Configuration
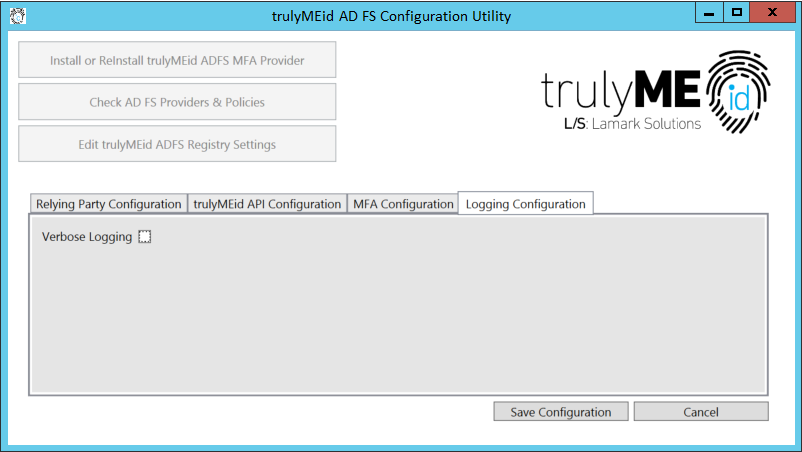
If Verbose Logging is enabled, trulyMEid will record detailed information to the event log. This is typically useful in debugging, and should be turned off in production environments. (HKLM\SOFTWARE\trulyMEid\VerboseLogging set to either “true” or “false”)
Configure AD FS
In the AD FS admin console, navigate to Authentication Policies, and click Edit next to the Global Settings in the Multi-Factor Authentication section.
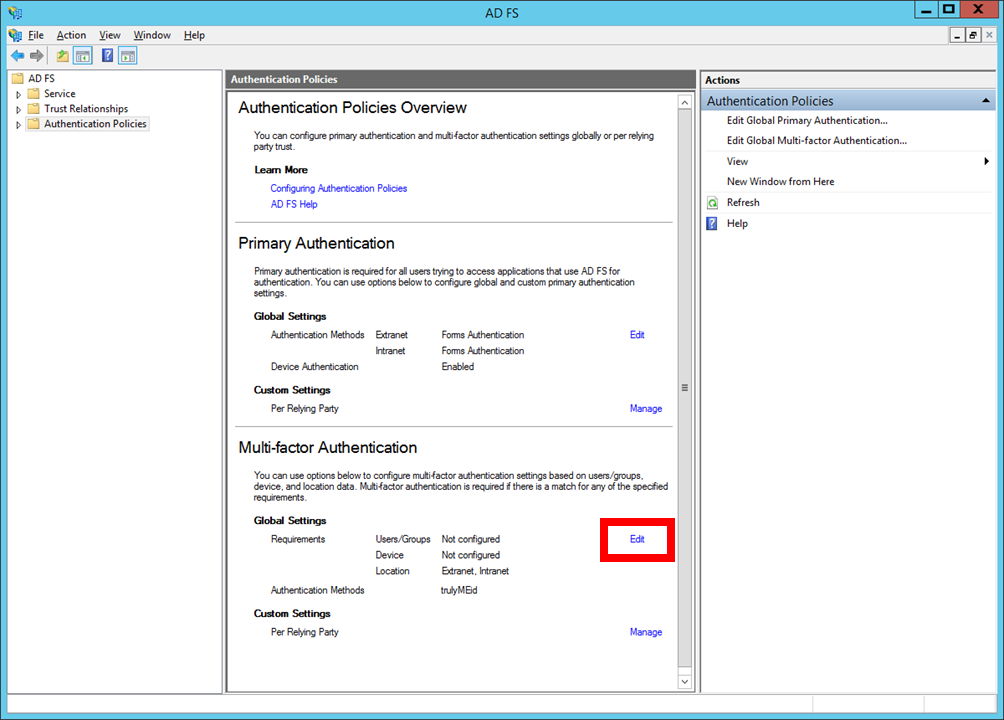
In the “Edit Global Authentication Policy” popup, check the box next to “trulyMEid” under the “Select additional authentication methods.”
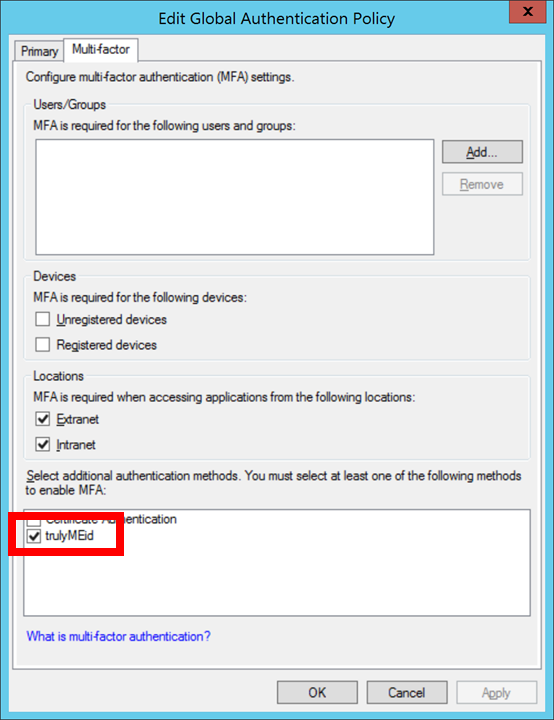
Configure global or individual applications for MFA via trulyMEid as you would any other MFA provider in AD FS.
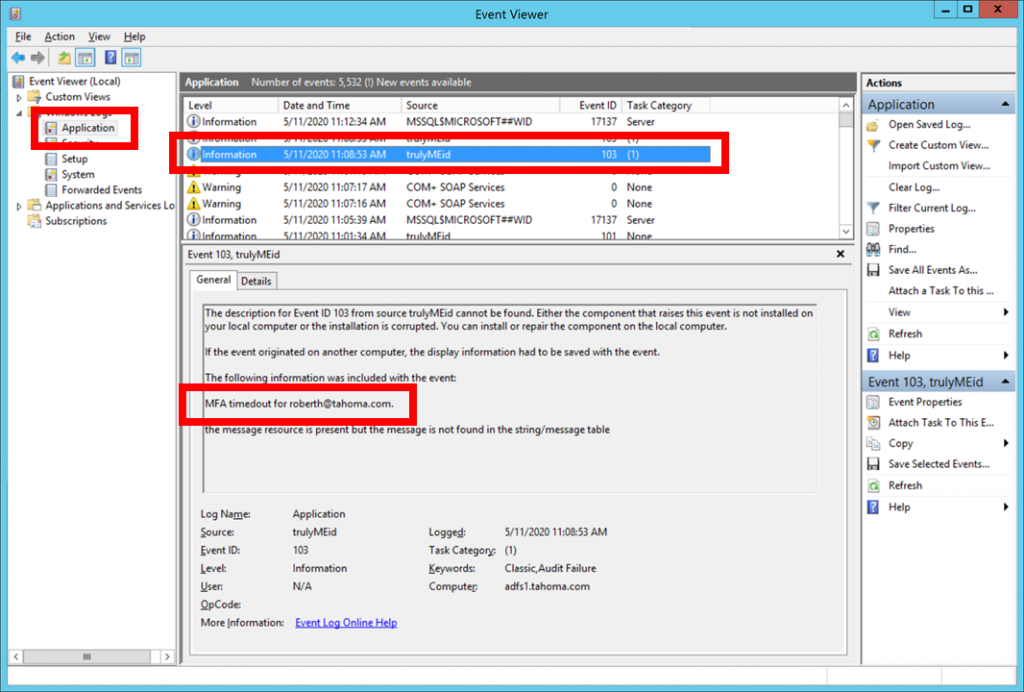
Event Logs
trulyMEid events appear in the Application log on the AD FS server under “trulyMEid” as the Source of the event.
Categories
| Category # | Category Description |
| 1 | MFA Event (Approved, Denied, Timedout) |
| 2 | User Lookup Issue |
| 3 | Network Connection Issue |
| 4 | Unexpected Error |
| 5 | Verbose Message |
Event IDs
| Event ID | Event Description |
| 101 | MFA Approved (i.e. user tapped VERIFY) |
| 102 | MFA Denied (i.e. user tapped CANCEL) |
| 103 | MFA Timedout (i.e. no response from user) |
| 201 | Unknown user (i.e. the email address does not exist in the trulyMEid system) |
| 202 | Expired ID (i.e. the user has an ID but it’s expired) |
| 203 | No ID (i.e. the user has not been issued an ID) |
| 204 | No active devices (i.e. the user does not have any active devices) |
| 301 | Network transport layer connectivity issue (check API configuration items) |
| 401 | Unexpected error from the trulyMEid cloud (check Relying Party configuration items) |
| 501 | Verbose logging message |
