Insider Threat & Ransomware
Identifying the Insider Threat
Cyber attacks hit businesses every day. Former Cisco CEO John Chambers once said, “There are two types of companies: those that have been hacked, and those who don’t yet know they have been hacked.” According to the ISAC (Information Systems Audit and Control Association) the total volume of events has increased almost 400% between January 2016 and January 2021. . Often, attackers are looking for ransom: Over 50 percent of ransomware cyber attacks resulted in ransom damages of $4,500,000 or more.
No industry is immune to the attacks, from financial institutions, and hospitals to professional service companies.
Cybercrime increases every year as people attempt to exploit vulnerable business systems. Cyberthreats can also be launched with ulterior motives. Some attackers look to obliterate systems and data as a form of “hacktivism” or employee aggression. Recent forms of ransomware have proved to involve employee activism and insider attack.
As digital systems are controlling more and more of our critical infrastructure, security convergence now engages IT, Physical Security, Operational Technology (OT) rolled into a cyber physical and procedural capability.
Our consolidated solution integrates with HR systems, IT systems, Operational Technology, and Physical Control Access systems. You can deliver a unified and proactive threat response to a wide range of incidents, with real time data connections across enterprise applications. You can manage the complete identity lifecycle from onboarding to out processing for your internal and external workforce, visitor’s and contractors and tie it directly to access governance for IT, physical and Operational work-spaces.
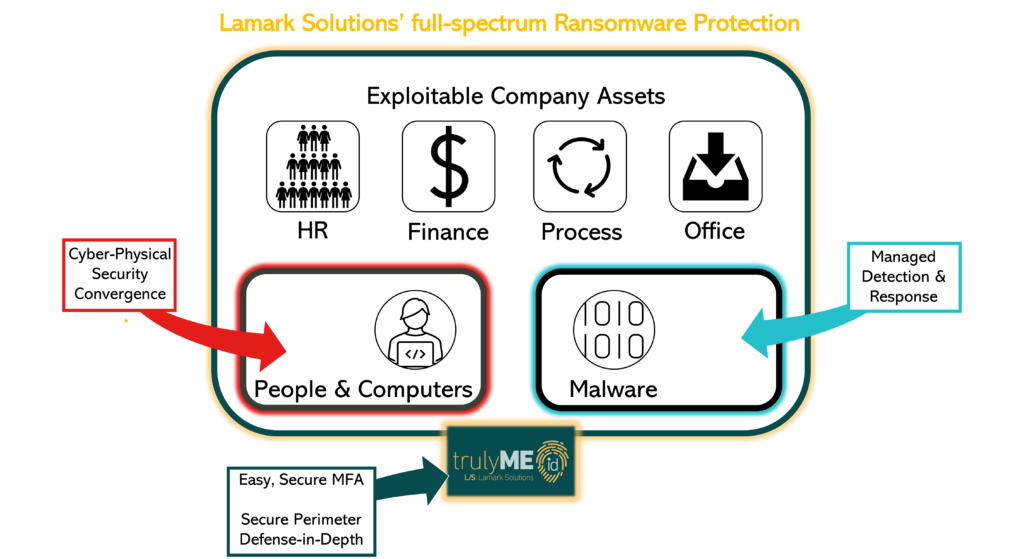
Key Capabilities Include
Identity Management and Governance Beyond IT
- Identity Life cycle management with automated workflow
- Access Certification and Authorization—Logical and Physical
- Contractor/Visitor management capabilities
- IT roles, Operational Technology roles and Physical Access Authorizations
Enable IT and Operational Consolidation to Protect Critical Infrastructure
- Role-based and User-based accesses
- Roles that should have corporate access and authorizations
- Roles that should have sensitive area access and authorizations
- Roles that have OT system access along with IT access
Build in Compliance and Active Policy Enforcement
- Automatic verification of training and background certification delivers real-time Rule Enforcement
Enterprise Scalability and Global Deployment
- The latest software solutions are designed to scale to hundreds of thousands of users
for large enterprise and global mission critical applications.
Risk Decisions into the Cyber Identity System
- Purpose-built risk analytics and risk management features go beyond traditional badging
- System capabilities. Risk decisions are easier to make with user attribute records, access patterns and even policy violation scores providing behavior anomalies. The system sends alerts on exceptions with custom reports and dashboards. Inside cyber and physical threats are trended early and highlighted to security personnel.
